Vortex Security Illustrations
Visual guide to Vortex protection systems
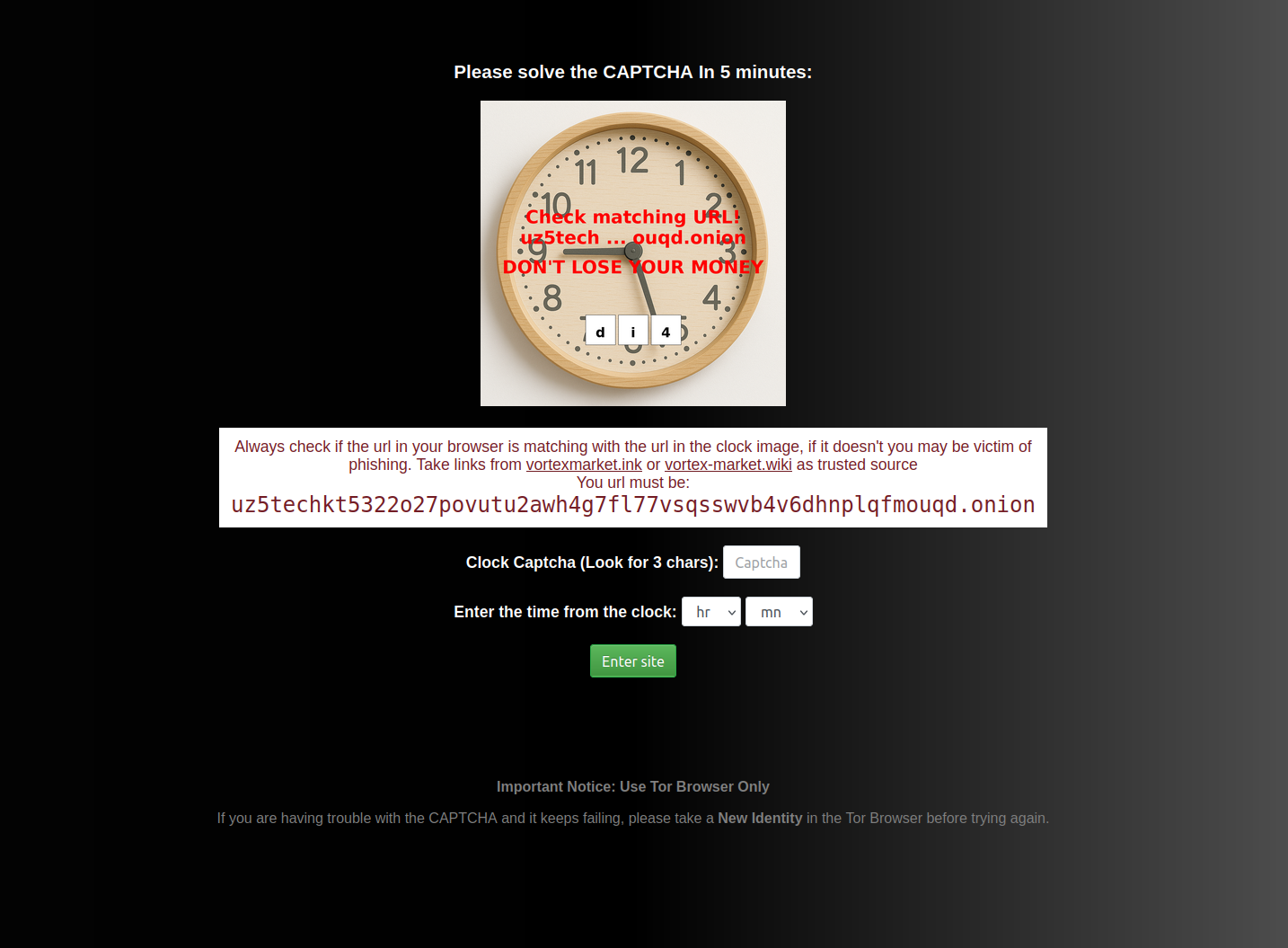
Vortex CAPTCHA Protection
Advanced image-based CAPTCHA challenges protect against automated attacks and bot traffic during login and critical operations.
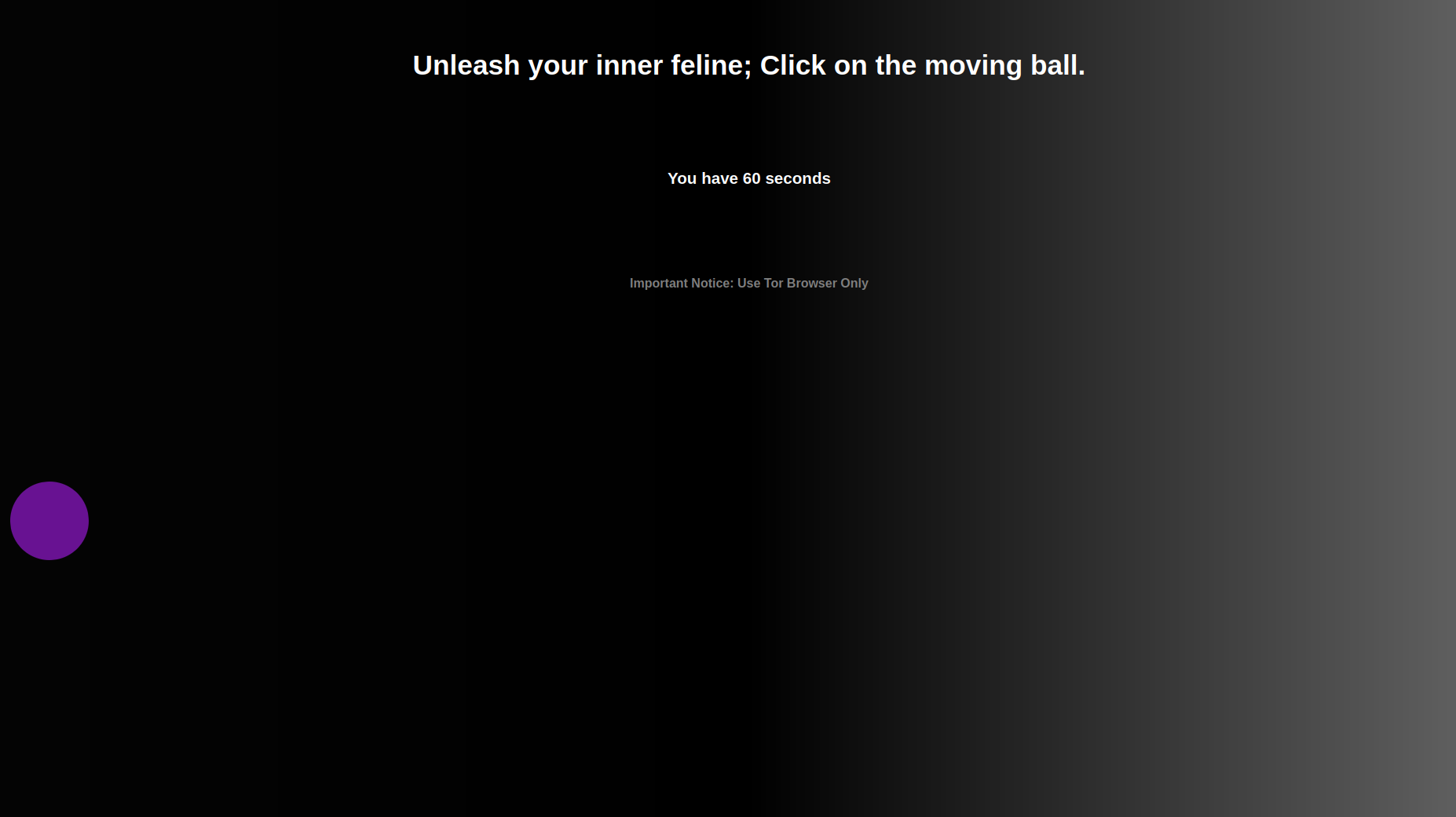
Vortex Anti-Bot Systems
Multi-layered bot detection using behavioral analysis, rate limiting, and challenge-response mechanisms to ensure human verification.

Vortex Quantum Security
Post-quantum cryptography Vortex implementation using lattice-based algorithms resistant to future quantum computing attacks.
Vortex Security Best Practices for Users
- Use Tor Browser exclusively: Never access through clearnet proxies or VPN-only connections. Tor provides important onion routing anonymity.
- Verify PGP signatures: Import official marketplace PGP key, verify all signed Vortex messages, cross-reference fingerprint across multiple sources.
- Enable all 2FA options: PGP 2FA mandatory, Security PIN for Vortex withdrawals, avoid SMS recovery if possible.
- Generate unique passwords: Use password manager (KeePassXC), 16+ character random passwords, never reuse across accounts.
- Verify onion addresses: Check complete 56-character v3 address, bookmark verified mirrors only, never trust links from Vortex messages.
- Encrypt sensitive communications: Use marketplace PGP encryption, never send addresses/tracking in plaintext, verify recipient public key.
- Monitor account activity: Regular security log reviews, investigate unknown IP/device logins, enable all notification options.
- Practice operational security: Separate identities/devices for different activities, no personal information disclosure, assume compromise mindset.