Vortex Market: Next-Generation Marketplace Technology
Vortex Market emerged in October 2023 as a response to the evolving needs of privacy-conscious users. Built from the ground up with modern security standards, Vortex marketplace implements advanced technologies that distinguish it from earlier marketplace generations. The platform currently ranks among the top 10-15 active darknet marketplaces, serving between 5,000-20,000 monthly active users.
The Vortex platform architecture uses Tor v3 hidden services, providing enhanced cryptographic security with 56-character onion addresses that are self-authenticating and resistant to impersonation attacks. Unlike older marketplaces that retrofitted security features, Vortex was designed security-first, with quantum-resistant encryption protocols and multi-signature escrow systems integrated at the foundational level.
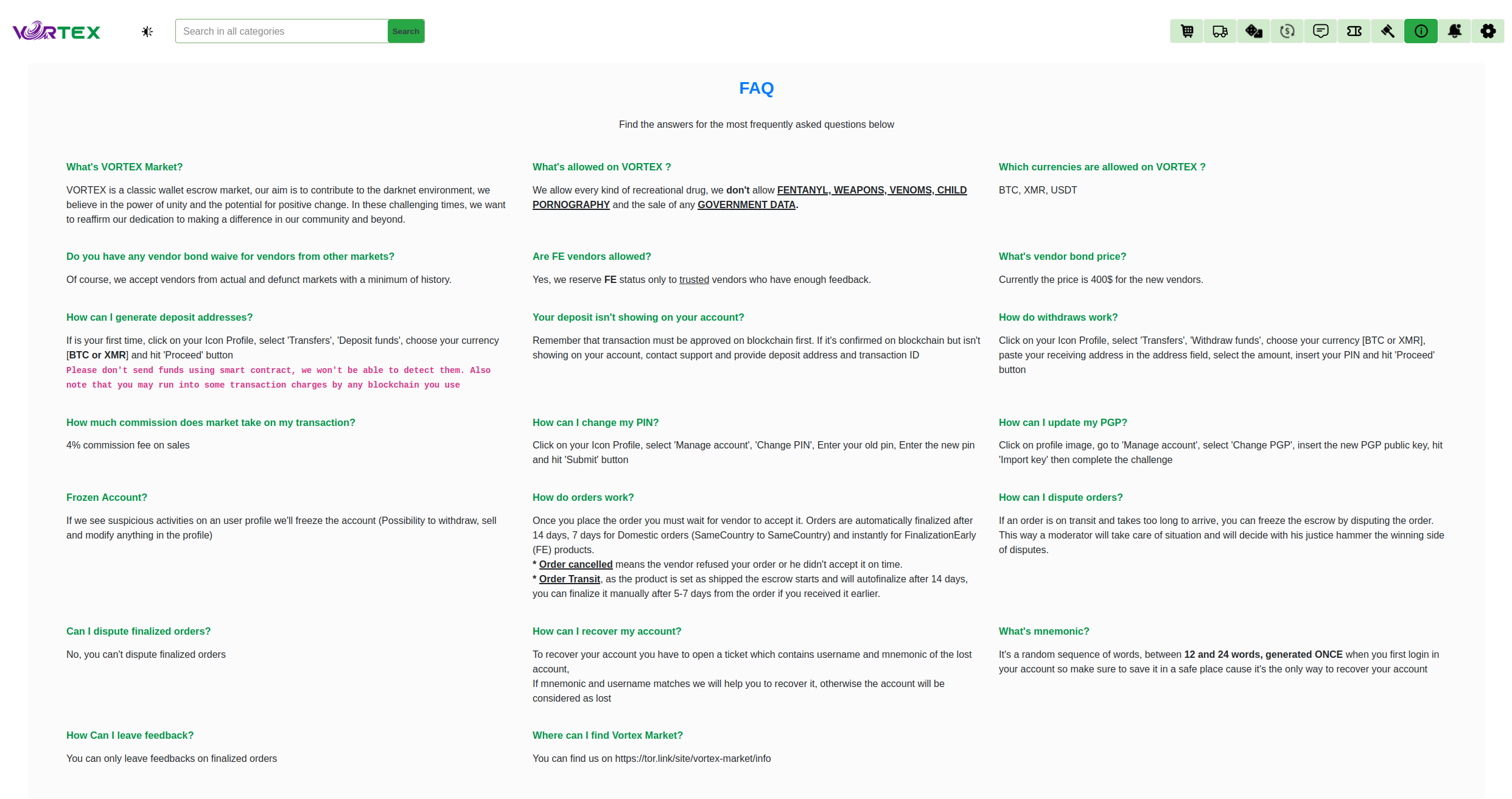
Six Cryptocurrency Support System
Vortex Market distinguishes itself through complete multi-currency support. The platform accepts Bitcoin (BTC) as the primary currency, Monero (XMR) for maximum privacy transactions, USDT stablecoin for price-stable trading, Litecoin (LTC) for faster confirmations, Ethereum (ETH) with smart contract compatibility, and Zcash (ZEC) for optional shielded transactions.
This multi-currency approach provides users with unprecedented flexibility. Privacy-focused users can use Monero's built-in privacy features (ring signatures, stealth addresses, RingCT) for completely untraceable transactions. Users concerned about cryptocurrency volatility can use USDT's price stability. Those prioritizing transaction speed can choose Litecoin's faster confirmation times. The automatic exchange rate conversion system updates in real-time from multiple sources, ensuring accurate pricing across all supported cryptocurrencies.
Advanced Security Architecture
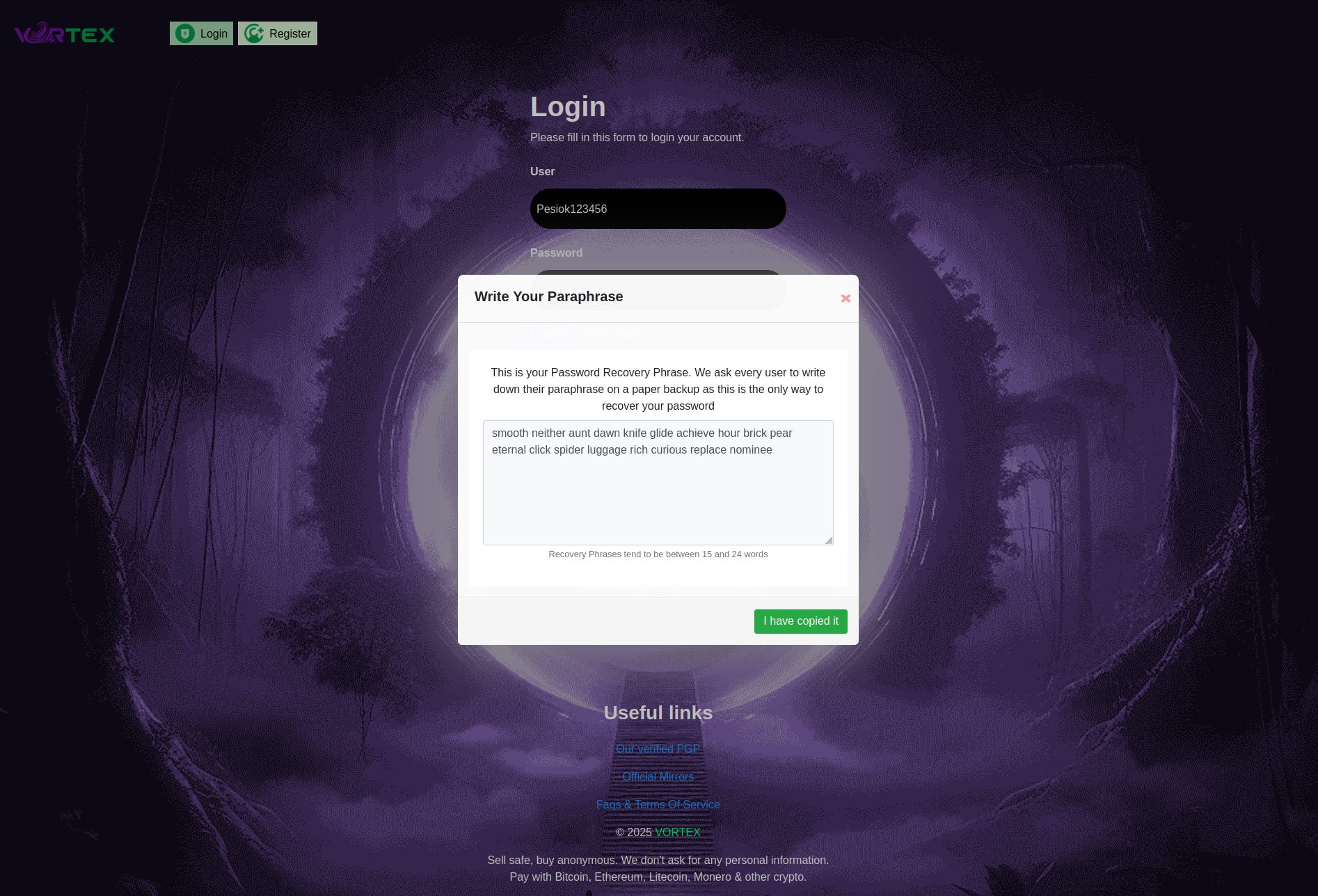
The Vortex security model implements four distinct authentication levels. Level 1 provides username and password with bcrypt hashing (12 rounds) and 60-minute session timeouts. Level 2 introduces PGP Two-Factor Authentication, mandatory for vendors and optional for buyers, where the server generates challenge tokens encrypted with users' public keys, requiring private key decryption within a 5-minute verification window.
Level 3 implements Security PIN protection, requiring a separate 6-8 digit code for withdrawals, password changes, and account deletion. This separation means that even if session credentials are compromised, critical operations require additional authentication. Level 4 provides optional email/SMS recovery, though security-conscious users often disable this potentially weaker authentication vector.
Vortex employs quantum-resistant cryptography through lattice-based encryption, specifically utilizing the CRYSTALS-Kyber protocol selected by NIST for post-quantum standardization. This forward-thinking approach protects against future quantum computing attacks that could potentially break current RSA and elliptic curve cryptography. The hybrid classical-quantum system combines RSA-4096 with lattice algorithms during the transition period, providing defense-in-depth against both current and future threats.
User Experience & Interface Design
Vortex Market features a modern, minimalist interface that prioritizes usability without compromising security. The clean dark theme (black #000000, dark gray #333333, blue accent highlights) reduces eye strain during extended sessions while maintaining excellent contrast for readability. The responsive layout adapts smoothly to desktop, laptop, and mobile devices, with page load times optimized to 2-5 seconds even over Tor connections.
The multi-column product grid layout with thumbnail previews enables efficient browsing. Advanced search and filtering capabilities include category-based navigation with subcategory drilling, full-text search across titles and descriptions, price range filters with multi-currency support, vendor reputation filtering, and shipping location filters. Saved search functionality provides alert notifications when matching products appear, helping users track specific items or price points.
Escrow Protection & Dispute Resolution
Vortex implements a reliable multi-signature escrow system requiring 2-of-3 signatures (buyer, vendor, marketplace) to release funds. This cryptographic architecture ensures no single party can unilaterally access escrowed funds. The 14-day automatic release countdown provides buyers ample time to receive and verify purchases before funds transfer to vendors.
The dispute resolution system allows both parties to submit encrypted evidence (images, messages, tracking information). Neutral arbitrators holding the third signature review submitted materials and release funds to the appropriate party based on evidence. This transparent system (with anonymized arbitration histories) provides accountability while protecting user privacy. Time-locked smart contracts and extension mechanisms accommodate complex orders requiring additional shipping time.
DDoS Protection & Uptime
Vortex employs sophisticated DDoS mitigation systems including queue management (30-60 second waiting rooms during attacks with position indicators), CAPTCHA challenges triggered on login and high-frequency actions, rate limiting per hashed IP address (100 requests per minute with progressive penalties), and Cloudflare-like services with Anycast network distribution. The infrastructure demonstrates moderate resilience, with typical recovery times of 30-120 minutes following targeted attacks, maintaining accessibility for legitimate users while filtering malicious traffic.